DOD Cybersecurity: Enhanced Attention Needed to Ensure Cyber Incidents Are Appropriately Reported and Shared
Fast Facts
Cyber attacks threaten national security—but hackers continue to target DOD as well as private companies and others involved in the nation's military operations.
DOD has taken steps to combat these attacks and has reduced the number of cyber incidents in recent years. But we found that DOD:
- Hasn't fully implemented its processes for managing cyber incidents
- Doesn't have complete data on cyber incidents that staff report
- Doesn't document whether it notifies individuals whose personal data is compromised in a cyber incident
Our recommendations address these issues.
Ensuring the cybersecurity of the nation is on our High Risk list.

Highlights
What GAO Found
The Department of Defense (DOD) and our nation's defense industrial base (DIB)—which includes entities outside the federal government that provide goods or services critical to meeting U.S. military requirements—are dependent on information systems to carry out their operations. These systems continue to be the target of cyber attacks, as DOD has experienced over 12,000 cyber incidents since 2015 (see figure).To combat these incidents, DOD has established two processes for managing cyber incidents—one for all incidents and one for critical incidents. However, DOD has not fully implemented either of these processes.
Cyber Incidents Reported by Department of Defense's Cyber Security Service Providers from Calendar Years 2015 through 2021
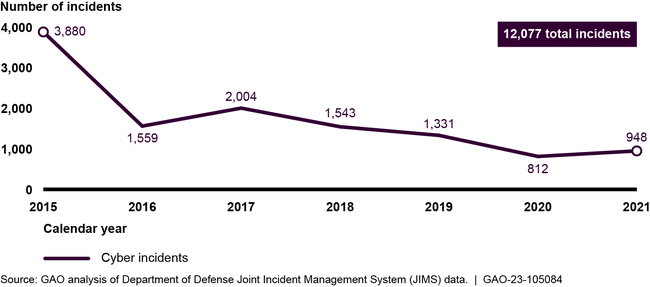
Despite the reduction in the number of incidents due to DOD efforts, weaknesses in reporting these incidents remain. For example, DOD's system for reporting all incidents often contained incomplete information and DOD could not always demonstrate that they had notified appropriate leadership of relevant critical incidents. The weaknesses in the implementation of the two processes are due to DOD not assigning an organization responsible for ensuring proper incident reporting and compliance with guidance, among other reasons. Until DOD assigns such responsibility, DOD does not have assurance that its leadership has an accurate picture of the department's cybersecurity posture.
In addition, DOD has not yet decided whether DIB cyber incidents detected by cybersecurity service providers should be shared with all relevant stakeholders, according to officials. DOD guidance states that to protect the interests of national security, cyber incidents must be coordinated among and across DOD organizations and outside sources, such as DIB partners. Until DOD examines whether this information should be shared with all relevant parties, there could be lost opportunities to identify system threats and improve system weaknesses.
DOD has established a process for determining whether to notify individuals of a breach of their personally identifiable information (PII). This process includes conducting a risk assessment that considers three factors—the nature and sensitivity of the PII, likelihood of access to and use of the PII, and the type of the breach. However, DOD has not consistently documented the notifications of affected individuals, because officials said notifications are often made verbally or by email and no record is retained. Without documenting the notification, DOD cannot verify that people were informed about the breach.
Why GAO Did This Study
DOD and DIB information technology systems continue to be susceptible to cyber incidents as cybersecurity threats have evolved and become more sophisticated. Federal laws and DOD guidance emphasize the importance of properly reporting and sharing cyber incident information, as both are vital to identifying system weaknesses and improving the security of the systems.
House Report 116-442 included a provision for GAO to review DOD's cyber incident management. This report examines the extent to which DOD established and implemented a process to (1) report and notify leadership of cyber incidents, (2) report and share information about cyber incidents affecting the DIB, and (3) notify affected individuals of a PII breach.
To conduct this work, GAO reviewed relevant guidance, analyzed samples of cyber incident artifacts and cyber incident reports submitted by the DIB and privacy data breaches reported by DOD, and surveyed 24 DOD cyber security service providers. In addition, GAO interviewed officials from DOD and cyber security service providers and convened two discussion groups with DIB companies.
Recommendations
GAO is making six recommendations, including that DOD assign responsibility for ensuring proper incident reporting, improve the sharing of DIB-related cyber incident information, and document when affected individuals are notified of a PII breach. DOD concurred with the recommendations.
Recommendations for Executive Action
| Agency Affected | Recommendation | Status |
|---|---|---|
| Department of Defense | The Secretary of Defense should ensure that the DOD CIO, Commander of CYBERCOM, and Commander of JFHQ-DODIN assign responsibility for overseeing cyber incident reporting and leadership notification, and ensuring policy compliance. (Recommendation 1) |
DOD concurred with the recommendation. According to documentation we reviewed, DOD has clarified who should have responsibility for overseeing cyber incident reporting and leadership notification. On August 9, 2023, DOD CIO issued DOD Instruction 8530.CE "Cyber Incident Response" which clarifies policy, responsibilities, and procedures for the DoD cyber incident response. Additionally, DOD Instruction 8530.03 para 2.11.h and 2.11.l.(2) assigns the notification of leadership responsibility to the Commander of CYBERCOM and DOD Directive 5144.02 "DoD Chief Information Officer (DoD CIO)" para 3.g assigns the CIO the responsibility for providing guidance and oversight for DoD network operations, including the standards for day-to-day defense and protection of DoD information networks; DoD IT support to military and joint missions; and resilience and reliability of information and communication networks." The actions taken by DOD meet the intent of our recommendation.
|
| Department of Defense | The Secretary of Defense should ensure that the DOD CIO, Commander of CYBERCOM, and Commander of JFHQ-DODIN align policy and system requirements to enable DOD to have enterprise-wide visibility of cyber incident reporting to support tactical, strategic, and military strategies for response. (Recommendation 2) |
DOD concurred with the recommendation. On August 9, 2023, the DOD CIO issued DOD Instruction 8530.CE "Cyber Incident Response" which clarifies policy, responsibilities, and procedures for the DoD cyber incident response. DOD is developing a larger Unified Platform with planned applications to be developed to increase collaboration. Deliberate efforts are being made to perform automated reporting into JIMS, to meet CJCSM 6510.0lB policy/guidance, while also providing timely enterprise-wide visibility of cyber incidents/events. DOD's estimated completion date is 06/30/2025. We will continue to monitor DOD's efforts.
|
| Department of Defense | The Secretary of Defense should ensure that the DOD CIO, Commander of CYBERCOM, and Commander of JFHQ-DODIN include in new guidance on incident reporting include detailed procedures for identifying, reporting, and notifying leadership of critical cyber incidents. (Recommendation 3) |
DOD concurred with the recommendation. On August 9, 2023, DOD CIO issued DOD Instruction 8530.CE "Cyber Incident Response" which clarifies policy, responsibilities, and procedures for the DOD cyber incident response. USCYBERCOM plans to update its instruction/Manual to supplement CJCSM 6510.01B by providing operational guidance for cyberspace incident reporting of activities on the DOD IN and assist with reforming enterprise-wide strategies, and processes for reporting cyber incidents and events (e.g., summaries, major cyber incidents, trends, enterprise-wide issues). Estimated completion date for the manual is 06/20/2025. We will continue to monitor DOD's efforts.
|
| Department of Defense | The Secretary of Defense should ensure that the Commander of CYBERCOM—in coordination with DOD CIO and Directors of DC3 and DCSA—examines whether information on DIB-related cyber incidents handled by CSSPs is relevant to the missions of other DOD components, including DC3 and DCSA, and identifies when and with whom such information should be shared. (Recommendation 4) |
DOD concurred with the recommendation. According to documentation we reviewed, DOD has clarified when and with whom DIB-related cyber incidents handled by CSSPs should be shared. Starting in 2023, the DOD CIO, DC3, DCSA, and USCYBERCOM started to engage each other on how cyber incident information should be shared bi-directionally and in a timely manner in the Joint Incident Management System (JIMS). For example, the DC3 representative to the USCC JOC Ops Enablement Cell (OEC) briefs Mandatory Incident Reports (MIRs) twice weekly at the OEC collaboration meetings which includes representatives from USCC/NSA JOC and many other DOD, USG and law enforcement/counter-intelligence organizations. In addition, in July 2024, DC3 started adding the USCC Cyber Battle Captains to the Cyber Incident Notification pre-pub process to receive notification of high-profile DIB incidents. The actions taken by DOD meet the intent of our recommendation.
|
| Department of Defense | The Secretary of Defense should ensure that the DOD CIO determines what actions need to be taken to encourage more complete and timely mandatory cyber incident reporting from DIB companies. (Recommendation 5) |
DOD concurred with the recommendation. According to documentation we reviewed, DOD has taken and continues to take actions to encourage complete and timely mandatory cyber incident reporting from DIB companies. Starting in May 2023, DOD began to provide ongoing educational briefings to the DIB on the importance of cyber incident reporting & response. In addition, DOD continues to engage the DIB with Cybersecurity-as-a-Service (CSaaS) capabilities provided by DOD to eligible DIB companies, as appropriate and authorized, at no-cost. These capabilities aide in automatically detecting and blocking malicious cyber activity, with the impact of reducing the number of cyber incidents occurring to DIB companies, and thus, reducing a reporting burden. The actions taken by DOD meet the intent of our recommendation.
|
| Department of Defense | The Secretary of Defense should ensure—through the Director of the Privacy, Civil Liberties, and Freedom of Information Directorate—that DOD components document instances where individuals affected by a privacy data breach were notified. (Recommendation 6) |
DOD concurred with the recommendation. According to documentation we reviewed, DOD has developed an information system for documenting that individuals affected by a privacy data breach were notified of the breach. In order to ensure that DoD components document instances where individuals affected by a privacy data breach are notified, the Office of the Assistant to the Secretary of Defense for Privacy, Civil Liberties, and Transparency designed, developed, and launched the Defense Privacy Information Management System (DPIMS) with full operational capability on 22 June 2023. DPIMS has been designed to capture the type of notification, as well as maintain a copy of the notification as an artifact for the breach. DPIMS successfully achieved full operational capability (FOC) on 29 April 2024. The actions taken by DOD meet the intent of our recommendation.
|
