Cybersecurity and Infrastructure Security Agency: Actions Needed to Ensure Organizational Changes Result in More Effective Cybersecurity for Our Nation
Fast Facts
A 2018 federal law established the Cybersecurity and Infrastructure Security Agency to help protect critical infrastructure from cyber and other threats—but it isn't fully up and running yet.
CISA completed 2 of 3 phases in its organization plan, including defining an organizational structure. It also completed about a third of the tasks planned for the final phase by its December 2020 milestone.
Until CISA updates its milestones and fully implements its plans, it may be difficult for it to identify and respond to cybersecurity incidents, such as the major cyberattack reported in December 2020 that affected both government and private industry.

Highlights
What GAO Found
To implement the requirements of the Cybersecurity and Infrastructure Security Agency (CISA) Act of 2018, CISA leadership within the Department of Homeland Security launched an organizational transformation initiative. The act elevated CISA to agency status; prescribed changes to its structure, including mandating that it have separate divisions on cybersecurity, infrastructure security, and emergency communications; and assigned specific responsibilities to the agency. (See figure 1 below.) CISA completed the first two of three phases of its organizational transformation initiative, which resulted in, among other things, a new organization chart, consolidation of multiple incident response centers, and consolidation of points of contact for infrastructure security stakeholders. Phase three is intended to fully implement the agency's planned organizational changes.
Figure 1: Five Key Responsibilities Assigned to the Cybersecurity and Infrastructure Security Agency (CISA)
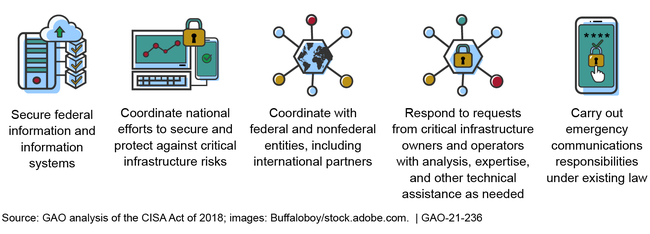
While CISA intended to fully implement the transformation by December 2020, it had completed 37 of 94 planned tasks for phase three by mid-February 2021. Among the tasks not yet completed, 42 of them were past their most recent planned completion dates. Included in these 42 are the tasks of finalizing the mission-essential functions of CISA's divisions and issuing a memorandum defining incident management roles and responsibilities across CISA. Tasks such as these appear to be critical to CISA's transformation initiative and accordingly its ability to effectively and efficiently carry out its cyber protection mission. In addition, the agency had not established an updated overall deadline for completing its transformation initiative. Until it establishes updated milestones and an overall deadline for its efforts, and expeditiously carries out these plans, CISA will be hindered in meeting the goals of its organizational transformation initiative. This in turn may impair the agency's ability to identify and respond to incidents, such as the cyberattack discovered in December 2020 that caused widespread damage.
Of 10 selected key practices for effective agency reforms previously identified by GAO, CISA’s organizational transformation generally addressed four, partially addressed five, and did not address one. For example, CISA generally addressed practices related to using data and evidence to support its planned reforms and engaging its employees in the organizational change process. The agency partially addressed practices related to, for example, defining goals and outcomes and conducting workforce planning. Workforce planning is especially important for CISA, given the criticality of hiring and retaining experts who, among other things, can help identify and respond to complex attacks. CISA did conduct an initial assessment of its cybersecurity workforce in 2019; however, it is still working on analyzing capability gaps and determining how to best fill those gaps. Finally, CISA did not address the practice of ensuring that its employee performance management system was aligned with its new organizational structure and transformation goals. Until it fully addresses workforce planning and the five other practices that are either partially or not addressed, CISA’s ability to leverage its organizational changes to effectively carry out its mission will be hindered.
Selected government and private-sector stakeholders from the 16 sectors considered to be critical infrastructures, such as banking and financial institutions, telecommunications, and energy, reported a number of challenges in coordinating with CISA. (See figure 2.)
Figure 2: Cybersecurity and Infrastructure Security Agency (CISA) Coordination Challenges Reported by Stakeholders Representing the 16 Critical Infrastructure Sectors

CISA has activities under way to mitigate some of these challenges, including tracking stakeholder inquiries to monitor the timeliness of responses and delivering briefings with intelligence tailored to stakeholder needs. However, it has not developed strategies to clarify changes to its organizational structure, have consistent stakeholder involvement in the development of guidance, and distribute information to all key stakeholders. Organizational structure and information distribution are both considered new challenges associated with the reorganization of CISA. Developing strategies to mitigate these challenges could help provide CISA with assurance that its stakeholders are receiving the information and support needed to make decisions about risks facing the nation's critical infrastructures.
Why GAO Did This Study
Threats to the nation's critical infrastructures and the information technology systems that support them require a concerted effort among federal agencies; state, local, tribal, and territorial governments; and the private sector to ensure their security. The seriousness of the threat was reinforced by the December 2020 discovery of a cyberattack that has had widespread impact on government agencies, critical infrastructures, and private-sector companies.
Federal legislation enacted in November 2018 established CISA to advance the mission of protecting federal civilian agencies' networks from cyber threats and to enhance the security of the nation's critical infrastructures in the face of both physical and cyber threats. To implement this legislation, CISA undertook a three-phase organizational transformation initiative aimed at unifying the agency, improving mission effectiveness, and enhancing the workplace experience for CISA employees.
GAO was asked to review CISA's organizational transformative initiative and its ability to coordinate effectively with stakeholders. The objectives of GAO's review were to (1) describe CISA's organizational transformation initiative, (2) assess the current progress of the initiative, (3) determine the extent to which CISA's transformation efforts align with key practices for effective agency reform, and (4) identify any challenges in CISA's coordination with stakeholders, and assess strategies the agency has developed to address such challenges.
To do this, GAO reviewed relevant information on CISA's efforts to develop an organizational transformation initiative to meet the requirements of the CISA Act of 2018. To assess the progress of CISA's efforts, GAO analyzed agency documentation to determine the status of activities related to the three phases of the organizational transformation and reasons for any delays in its progress. GAO also assessed CISA's efforts against selected key practices identified by GAO that can contribute to the effectiveness of agency reform efforts. In addition, GAO interviewed selected stakeholders related to CISA's primary mission areas to identify any pertinent challenges and analyzed strategies CISA developed to address these challenges.
Recommendations
GAO is making 11 recommendations to CISA:
- Establish new expected completion dates for the phase three tasks that are past their completion dates, with priority given to tasks critical to mission effectiveness.
- Establish an overall deadline for the completion of the transformation initiative.
- Fully address each of the six reform practices that have been either partially or not addressed.
- Develop strategies to mitigate each of the three infrastructure challenges that remain outstanding.
The Department of Homeland Security agreed with GAO's recommendations.
Recommendations for Executive Action
| Agency Affected | Recommendation | Status |
|---|---|---|
| Department of Homeland Security |
Priority Rec.
The Director of CISA should establish expected completion dates for those phase three tasks that are past their completion dates, with priority given to those tasks critical to mission effectiveness. (Recommendation 1) |
CISA concurred with this recommendation. In March 2021 agency leadership issued a memorandum that directed several actions to transition transformation activities into operational tasks for implementation by CISA's divisions and mission support offices. In May 2023, CISA provided documentation showing that it had allocated responsibility for the remaining phase three tasks and established expected completion dates for them. Accordingly, we consider this recommendation to be implemented. By taking these steps, CISA will be better positioned to complete its organizational transformation without additional delays, enhancing its mission effectiveness.
|
| Department of Homeland Security |
Priority Rec.
The Director of CISA should establish an overall deadline for the completion of the transformation initiative. (Recommendation 2) |
CISA concurred with this recommendation. In March 2021, agency leadership issued a memorandum that directed several actions to transition transformation activities into operational tasks for implementation by CISA's divisions and mission support offices. According to CISA, this constituted the end of phase three of its transformation effort. In May of 2023, CISA provided documentation showing how it had allocated responsibility for the remaining tasks for the transformation initiative and established planned completion dates. Further, CISA established an overall deadline for the completion of these tasks of the end of December 2023. Accordingly, we consider this recommendation to be implemented. By taking these steps, CISA will be better positioned to complete its organizational transformation without additional delays, enhancing its mission effectiveness.
|
| Department of Homeland Security | The Director of CISA should establish plans, including time frames, for developing outcome-oriented performance measures to gauge the extent to which the agency's efforts are meeting the goals of the organizational transformation. (Recommendation 3) |
CISA concurred with this recommendation. In March 2023, we verified CISA had established such performance measures. Specifically, CISA detailed goals and sub-goals in its most recent strategic plan, and several of these relate to the goals of its organizational transformation. For each of these goals, the plan identifies a measurement approach and representative outcomes. Further, the agency defined various output and outcome measures supporting each of these goals and sub-goals. Accordingly, we consider this recommendation to be implemented. By taking these steps, CISA is better positioned to gauge the extent to which its efforts are meeting the goals of its organizational transformation.
|
| Department of Homeland Security | The Director of CISA should collect input to ensure that organizational changes are aligned with the needs of stakeholders, taking into account coordination challenges identified in this report. (Recommendation 4) |
CISA concurred with this recommendation. Since then, CISA has taken steps to collect stakeholder input on its products and services to ensure that its organizational changes are aligned with stakeholder needs. Specifically, CISA established a Stakeholder Relationship Management program to manage and share stakeholder engagement data across the agency through a central tool, which is to provide CISA with the capability to leverage integrated stakeholder engagement data to improve mission delivery. Further, CISA deployed a stakeholder Service Change Request Tool to collect feedback about CISA's suite of services and connect them to CISA's Divisions and Mission Enabling Offices to review, approve, and to take action as requested. According to CISA officials, the process CISA has established, to include its stakeholder relationship management program and tools such as its Service Change Request tool, allow it to evaluate the extent to which its products and services, as well as organizational changes, are aligned with the needs of its stakeholders. In addition, they stated that that this feedback will be used to inform future modifications to its organization, as warranted. Accordingly, we consider this recommendation to be implemented.
|
| Department of Homeland Security | The Director of CISA should establish processes for monitoring the effects of efforts to reduce fragmentation, overlap, and duplication including identifying potential cost savings. (Recommendation 5) |
CISA concurred with this recommendation. In July 2023, CISA provided an internal report summarizing a study it performed on the effects of the CISA reorganization on fragmentation, overlap, and duplication at the agency. In addition, CISA established quarterly division management reviews (DMRs) as an opportunity for divisions to have collaborative, transparent discussions with leadership while examining each division's data wholistically. The DMRs provide an in-depth look into the performance of CISA divisions across mission areas, as well as budget, staffing, acquisitions, and other programmatic areas. These reviews provide a chance for coordination on any areas of duplication, fragmentation, and overlap, thus resulting in identification of areas for cost savings. CISA further provided evidence that issues of duplication and cost savings were on the discussion agendas for these meetings. Accordingly, we consider this recommendation to be implemented.
|
| Department of Homeland Security | The Director of CISA should establish an approach, including time frames, for measuring outcomes of the organizational transformation, including customer satisfaction with organizational changes. (Recommendation 6) |
CISA concurred with this recommendation and has taken steps to collect input on stakeholder needs with respect to CISA's organization. Specifically, CISA's Strategic Plan for FY 2023-25 includes performance measures and representative outcomes related to the goals of its organizational transformation. In addition, the agency's Stakeholder Engagement Strategic Plan for FY 2023-25 includes, as one of its goals, that stakeholders' insights and feedback inform CISA product development and mission delivery. Further, starting January 2025, CISA intends to launch the CISA Stakeholder Impact Survey, in partnership with the CISA Stakeholder Feedback Working Group, as a tool to collect input from customers in order to identify customers' satisfaction with services, products, and events and assess progress in meeting the goals of the agency's strategic plan. CISA officials noted that this information may be used to inform any future organizational changes. Accordingly, we consider this recommendation to be implemented. By taking these steps, CISA is better positioned to enhance the effectiveness of its coordination with critical stakeholders.
|
| Department of Homeland Security | The Director of CISA should develop a strategy for comprehensive workforce planning. (Recommendation 7) |
CISA concurred with this recommendation. In December 2022, CISA provided evidence that it developed a workforce planning strategy. Specifically, the strategy defines CISA's strategic workforce goals, objectives, and priorities; workforce planning methodology; workforce planning lifecycle; planning, programming, budgeting & execution integration resource allocation plan; manpower requirements and resources; and challenges and risks. Accordingly, we consider this recommendation to be implemented. By developing this strategy, CISA should be better able to ensure that its workforce planning aligns with its current and emerging mission and programmatic goals.
|
| Department of Homeland Security | The Director of CISA should take steps to align the agency's employee performance management system with its organizational changes and associated goals. (Recommendation 8) |
CISA concurred with this recommendation. In December 2022, CISA provided evidence that it had taken steps to align its performance management system with its organizational changes and goals. Specifically, CISA issued a policy that establishes the Employee Performance Management Program for General Schedule employees, which is intended to promote and sustain a high-performance culture and results-oriented workforce within CISA. In addition, CISA's performance management program instruction provides standards, procedures and tools to execute the program. This includes, among other things, core competencies for employees that support the agency's mission priorities. Accordingly, we consider this recommendation to be implemented. By taking these steps, CISA is better positioned to ensure that its performance management program supports the goals of the agency's organizational transformation.
|
| Department of Homeland Security | The Director of CISA should communicate relevant organizational changes to selected critical infrastructure stakeholders to ensure that these stakeholders know with whom they should be coordinating in CISA's organization. (Recommendation 9) |
CISA concurred with this recommendation and has several efforts working in tandem to broadcast relevant organizational changes and to ensure stakeholders are connected to the proper CISA subject matter experts. These include goals and sub-goals in its Stakeholder Engagement Strategic Plan that are aimed at ensuring CISA's activities are aligned with stakeholder needs. Further, CISA revamped its service catalog and website directing users to tailored content directing users to the appropriate services and points of contact. Accordingly, we considered this recommendation to be implemented. By taking these steps, CISA has better ensured that stakeholders are able to access the services and staff at CISA who can help meet their needs.
|
| Department of Homeland Security | The Director of CISA should take steps, with stakeholder input, to determine how critical infrastructure stakeholders should be involved with the development of guidance for their sector. (Recommendation 10) |
CISA concurred with this recommendation and stated that it has determined to work primarily through the Sector and Government Coordinating Councils, to include workshops and emails, as the means to which they involve critical infrastructure stakeholders in the development of guidance for their respective sectors. In October 2023, CISA provided documentation of a feedback workshop summary and emails with critical infrastructure partners, as mechanisms and steps taken to solicit stakeholder input on sector guidance. This included input from over a hundred participants across sectors such as energy, IT, transportation, and financial services, among others. Additionally, CISA requested feedback from specific agencies as it pertained to their preliminary draft of the 2023 Sector Risk Assessment Guidance to enhance the security and resilience of the critical infrastructure. Accordingly, we consider this recommendation to be implemented. By taking these steps, with the consider of stakeholders, CISA is better positioned to identify opportunities to incorporate sector-specific expertise and develop guidance tailored to the needs of the various sectors.
|
| Department of Homeland Security | The Director of CISA should assess the agency's methods of communicating with its critical infrastructure stakeholders to ensure that appropriate parties are included in distribution lists or other communication channels. (Recommendation 11) |
CISA concurred with this recommendation. CISA updated the Federal Senior Leadership Council (FSLC) charter, including additional clarification concerning Sector Risk Management Agency (SRMA) roles and responsibilities. In particular, the charter specified that the purpose of FSLC is to coordinate the shared responsibilities of federal departments and agencies with responsibility for critical infrastructure security and resilience, as well as encourage communication and cooperation between those designated as SRMAs and non-SRMA specialized or supporting agencies. It further specified the council's approach to communication among its stakeholders. In October 2023, CISA provided evidence of the agency's use of email distribution lists as one of the various channels to communicate with stakeholders and to disseminate information with relevant subdivisions. Accordingly, we consider this recommendation to be implemented. By taking these steps, CISA is better positioned to ensure stakeholders are receiving needed information to manage risks to critical infrastructure.
|
