Critical Infrastructure Protection: Actions Needed to Address Significant Weaknesses in TSA's Pipeline Security Program Management
Fast Facts
The nation depends on the interstate pipeline system to deliver oil, natural gas, and more. This increasingly computerized system is an attractive target for hackers and terrorists. (Protection of cyber critical infrastructure is on our High Risk List.)
We found weaknesses in how TSA manages its pipeline security efforts. For example, it has no process for determining when to update its guidelines for pipeline operators. Also, its method for assessing risks needs updating.
We made 10 recommendations, including establishing better processes for updating guidelines and assessing risks.
Map of Hazardous Liquid and Natural Gas Pipelines in the United States, September 2018
This map of the United States shows the massive network of pipelines.
Highlights
What GAO Found
Pipeline operators reported using a range of guidelines and standards to address physical and cybersecurity risks, including the Department of Homeland Security's (DHS) Transportation Security Administration's (TSA) Pipeline Security Guidelines, initially issued in 2011. TSA issued revised guidelines in March 2018 to reflect changes in the threat environment and incorporate most of the principles and practices from the National Institute of Standards and Technology's Framework for Improving Critical Infrastructure Cybersecurity. However, TSA's revisions do not include all elements of the current framework and TSA does not have a documented process for reviewing and revising its guidelines on a regular basis. Without such a documented process, TSA cannot ensure that its guidelines reflect the latest known standards and best practices for physical security and cybersecurity, or address the dynamic security threat environment that pipelines face. Further, GAO found that the guidelines lack clear definitions to ensure that pipeline operators identify their critical facilities. GAO's analysis showed that operators of at least 34 of the nation's top 100 critical pipeline systems (determined by volume of product transported) deemed highest risk had identified no critical facilities. This may be due, in part, to the guidelines not clearly defining the criteria to determine facilities' criticality.
U.S. Pipeline Systems' Basic Components and Vulnerabilities
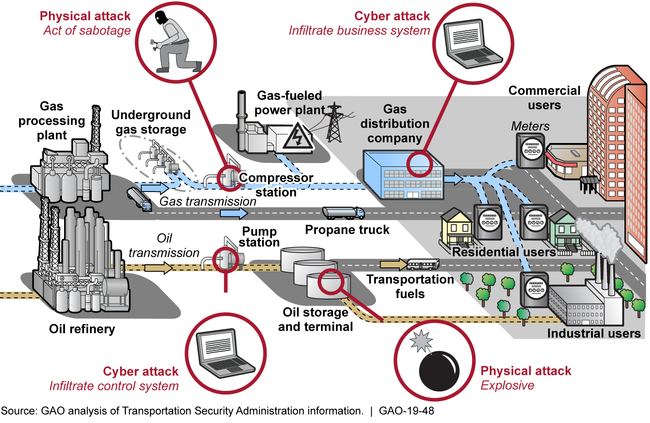
To assess pipeline security risks, TSA conducts pipeline security reviews—Corporate Security Reviews and Critical Facility Security Reviews—to assess pipeline systems' vulnerabilities. However, GAO found that the number of TSA security reviews has varied considerably over the last several years, as shown in the table on the following page.
Pipeline Security Reviews Conducted, Fiscal Year 2010 through July 2018
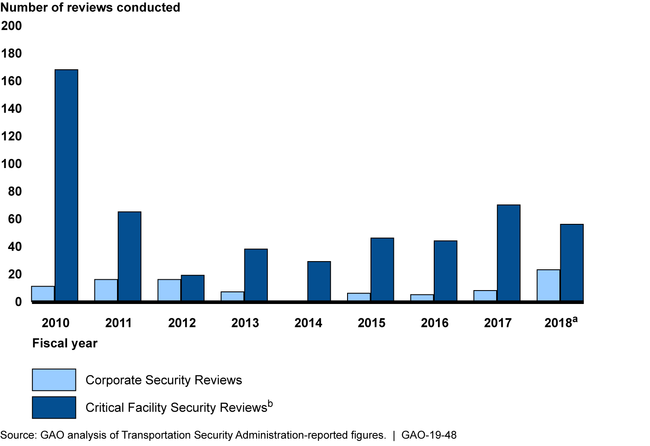
aFiscal year 2018 data are through July 31, 2018.
bFiscal years 2010 and 2011 represent Critical Facility Inspections—the predecessor of the Critical Facility Security Review.
TSA officials stated that staffing limitations have prevented TSA from conducting more reviews. Staffing levels for TSA's Pipeline Security Branch have varied significantly since fiscal year 2010 with the number of staff ranging from 14 full-time equivalents in fiscal years 2012 and 2013 to 1 in 2014. Further, TSA does not have a strategic workforce plan to help ensure it identifies the skills and competencies—such as the required level of cybersecurity expertise—necessary to carry out its pipeline security responsibilities. By establishing a strategic workforce plan, TSA can help ensure that it has identified the necessary skills, competencies, and staffing.
GAO also identified factors that likely limit the usefulness of TSA's risk assessment methodology for prioritizing pipeline system reviews. Specifically, TSA has not updated its risk assessment methodology since 2014 to reflect current threats to the pipeline industry. Further, its sources of data and underlying assumptions and judgments regarding certain threat and vulnerability inputs are not fully documented. In addition, the risk assessment has not been peer reviewed since its inception in 2007. Taking steps to strengthen its risk assessment, and initiating an independent, external peer review would provide greater assurance that TSA ranks relative risk among pipeline systems using comprehensive and accurate data and methods.
TSA has established performance measures to monitor pipeline security review recommendations, analyze their results, and assess effectiveness in reducing risks. However, these measures do not possess key attributes—such as clarity, and having measurable targets—that GAO has found are key to successful performance measures. By taking steps to ensure that its pipeline security program performance measures exhibit these key attributes, TSA could better assess its effectiveness at reducing pipeline systems' security risks. Pipeline Security Branch officials also reported conducting security reviews as the primary means for assessing the effectiveness of TSA's efforts to reduce pipeline security risks. However, TSA has not tracked the status of Corporate Security Review recommendations for the past 5 years. Until TSA monitors and records the status of these reviews' recommendations, it will be hindered in its efforts to determine whether its recommendations are leading to significant reduction in risk.
Why GAO Did This Study
More than 2.7 million miles of pipeline transport and distribute oil, natural gas, and other hazardous products throughout the United States. Interstate pipelines run through remote areas and highly populated urban areas, and are vulnerable to accidents, operating errors, and malicious physical and cyber-based attack or intrusion. The energy sector accounted for 35 percent of the 796 critical infrastructure cyber incidents reported to DHS from 2013 to 2015. Several federal and private entities have roles in pipeline security. TSA is primarily responsible for the oversight of pipeline physical security and cybersecurity.
GAO was asked to review TSA's efforts to assess and enhance pipeline security and cybersecurity. This report examines, among other objectives: (1) the guidance pipeline operators reported using to address security risks and the extent that TSA ensures its guidelines reflect the current threat environment; (2) the extent that TSA has assessed pipeline systems' security risks; and (3) the extent TSA has assessed its effectiveness in reducing pipeline security risks.
GAO analyzed TSA documents, such as its Pipeline Security Guidelines ; evaluated TSA pipeline risk assessment efforts; and interviewed TSA officials, 10 U.S. pipeline operators—selected based on volume, geography, and material transported—and representatives from five industry associations.
Recommendations
GAO makes 10 recommendations to TSA to improve its pipeline security program management (many are listed on the next page), and DHS concurred.
GAO recommends, among other things, that the TSA Administrator take the following actions:
implement a documented process for reviewing, and if deemed necessary, for revising TSA's Pipeline Security Guidelines at defined intervals;
clarify TSA's Pipeline Security Guidelines by defining key terms within its criteria for determining critical facilities;
develop a strategic workforce plan for TSA's Security Policy and Industry Engagement‘s Surface Division;
update TSA's pipeline risk assessment methodology to include current data to ensure it reflects industry conditions and threats;
fully document the data sources, underlying assumptions and judgments that form the basis of TSA's pipeline risk assessment methodology;
take steps to coordinate an independent, external peer review of TSA's pipeline risk assessment methodology;
ensure the Security Policy and Industry Engagement‘s Surface Division has a suite of performance measures which exhibit key attributes of successful performance measures; and
enter information on Corporate Security Review recommendations and monitor and record their status.
Recommendations for Executive Action
| Agency Affected | Recommendation | Status |
|---|---|---|
| Transportation Security Administration | The TSA Administrator should direct the Security Policy and Industry Engagement's Surface Division to implement a documented process for reviewing, and if deemed necessary, for revising TSA's Pipeline Security Guidelines at regular defined intervals. (Recommendation 1) |
We found that TSA's Pipeline Security Branch had revised its security guidelines in March 2018 to, among other things, reflect the dynamic threat environment and incorporate NIST's Cybersecurity Framework principles and practices. However, TSA had not instituted a documented process to consider the need to update the Pipeline Security Guidelines on a regular basis. As a result, we found that without a documented process defining how frequently TSA is to review and revise its guidelines, TSA could not ensure that its guidelines reflect the latest known standards and best practices for physical and cybersecurity. Therefore, we recommended that TSA implement a documented process for reviewing, and if deemed necessary, revising TSA's Pipeline Security Guidelines at regular defined intervals. In response, in March 2019 TSA officials established an internal operating procedure that documents the review and revision process for all of TSA's surface transportation security guidance, which include its Pipeline Security Guidelines. Per the procedure, TSA's Surface Division is to review, and if deemed appropriate revise, its surface transportation security guidance to ensure they remain current and appropriate using risk-based principles on an annual basis. Further, TSA's Surface Division is to update its security guidance, at a minimum, every five years but may update them earlier if TSA determines that new or revised are in the public interest. These actions are consistent with our recommendation.
|
| Transportation Security Administration | The TSA Administrator should direct the Security Policy and Industry Engagement's Surface Division to clarify TSA's Pipeline Security Guidelines by defining key terms within its criteria for determining critical facilities. (Recommendation 2) |
In December 2018, we reported on the Transportation Security Administration's (TSA) pipeline security program (GAO-19-48). During the course of our review, we found that TSA's Pipeline Security Guidelines for pipeline operators lacked clear definitions to ensure that pipeline operators identify their critical facilities. In addition, our analysis showed that operators of at least 34 of the nation's top 100 critical pipeline systems (determined by volume of product transported) deemed highest risk had identified no critical facilities. This might have been due, in part, to the guidelines not clearly defining the criteria to determine facilities' criticality. Consequently, we recommended that TSA clarify its TSA's Pipeline Security Guidelines by defining key terms within its criteria for determining critical facilities. In December 2020, TSA provided documentation and explanations for how critical facility terminology was updated in the guidelines. Examples of improved definitions include TSA's incorporation of existing regulatory terminology which pipeline stakeholders are already using and generally are familiar with, according to TSA officials. Pipeline industry stakeholders provided comments on draft versions of the redefined critical facility criteria and TSA officials reported meeting with pipeline industry associations who had direct input on the criteria. Based on our review of documentation reflecting the redefined criteria, pipeline operators will have a more clearly defined set of criteria with which to assess their systems and identify critical facilities. As a result, this recommendation is closed as implemented.
|
| Transportation Security Administration |
Priority Rec.
The TSA Administrator should develop a strategic workforce plan for its Security Policy and Industry Engagement's Surface Division, which could include determining the number of personnel necessary to meet the goals set for its Pipeline Security Branch, as well as the knowledge, skills, and abilities, including cybersecurity, that are needed to effectively conduct Corporate Security Reviews (CSR) and Critical Facility Security Reviews (CFSR). (Recommendation 3) |
In December 2018, we found that TSA had not established a workforce plan for its Pipeline Security Branch that identified staffing needs or cybersecurity skills required to best implement security reviews, such as the Corporate Security Reviews and Critical Facility Security Reviews. We recommended that TSA develop a strategic workforce plan that outlines the knowledge, skills, and abilities, including those related to cybersecurity, needed to effectively conduct pipeline security reviews. TSA's Human Capital Workforce Planning Division completed the Final Workforce Assessment Report in May 2021. The Assessment Report identified, among other things, several staffing inadequacies, particularly related to the pipeline cybersecurity mission. Specifically, the Assessment Report highlighted that the organization lacks qualified personnel with relevant skills, appropriate certifications, and/or expertise in cybersecurity and that over one-third of the agency's position descriptions were improperly classified for the duties required. In addition, the Assessment Report noted that TSA is short the necessary positions to perform the current and projected pipeline security mission, with a 41 percent increase in staffing needed to position the organization for mission success. The assessment includes a recommended workforce plan that defines short-term and long-term initiatives for addressing the staffing inadequacies. For example, the recommended workforce plan lists initiatives for developing and codifying specific staff duties required for physical or cybersecurity, budgeting to fund new staff position requirements, and collaborating with TSA's Human Capital office to recruit and hire needed staff. These actions help ensure that TSA is able to meet its mission of reducing pipeline systems' vulnerabilities to physical and cybersecurity risks, especially in a dynamic and evolving threat environment.
|
| Transportation Security Administration | The TSA Administrator should direct the Security Policy and Industry Engagement's Surface Division to update the Pipeline Relative Risk Ranking Tool to include up-to-date data to ensure it reflects industry conditions, including throughput and threat data. (Recommendation 4) |
In 2018, we found that the Pipeline Relative Risk Ranking Tool TSA uses to assess various security risks of pipeline systems had not been updated since 2014. For example, when the risk assessment was last updated in 2014, it used pipeline systems' throughput data from 2010 to assess relative risk. We determined that outdated data may limit the usefulness of the current risk assessment to allow the Pipeline Security Branch to effectively prioritize reviews of pipeline systems. As a result, we recommended that TSA update the Pipeline Relative Risk Ranking Tool to include up-to-date data to ensure it reflects industry conditions, including throughput and threat data. In December 2019, TSA provided an updated version of the Pipeline Relative Risk Ranking Tool. TSA explained that they used the most recent information available for specific data in the tool, even if that data may be several years old. To add clarity, TSA added the "effective date" of the data within the tool. Additionally, TSA made the determination that two years is an appropriate length of time for the assignment of a threat value. TSA's actions are consistent with our recommendation.
|
| Transportation Security Administration | The TSA Administrator should direct the Security Policy and Industry Engagement's Surface Division to fully document the data sources, underlying assumptions and judgments that form the basis of the Pipeline Relative Risk Ranking Tool, including sources of uncertainty and any implications for interpreting the results from the assessment. (Recommendation 5) |
We found that TSA had not fully documented sources of data and underlying assumptions and judgments regarding certain threat and vulnerability inputs for its Pipeline Relative Risk Ranking Tool. For example, the Pipeline Security Branch ranked threat equally across pipeline systems because officials said they did not have enough threat information to distinguish threat by pipeline. However, this judgment was not documented in the risk assessment's methodology. As a result, we recommended in December 2018 that TSA fully document the data sources, underlying assumptions and judgments that form the basis of the Pipeline Relative Risk Ranking Tool, including sources of uncertainty and any implications for interpreting the results from the assessment. In April 2020, TSA provided documentation and explanations of steps taken to address this recommendation. According to TSA officials and reflected in updated versions of the Pipeline Relative Risk Ranking Tool, TSA documented data sources, underlying assumptions and judgments, as well as potential sources of uncertainty in several areas. For example, TSA documented: multiple sources of threat information and implications for interpreting the threat data; data sources for pipeline interruption consequence information and discussions of assumptions regarding those sources; source dates for determining pipeline volumes of product flowing through the pipelines and discussion of related assumptions. TSA's actions are consistent with our recommendation.
|
| Transportation Security Administration |
Priority Rec.
The TSA Administrator should direct the Security Policy and Industry Engagement's Surface Division to identify or develop other data sources relevant to threat, vulnerability, and consequence consistent with the National Infrastructure Protection Plan and DHS critical infrastructure risk mitigation priorities and incorporate that data into the Pipeline Relative Risk Ranking Tool to assess relative risk of critical pipeline systems, which could include data on prior attacks, natural hazards, feedback data on pipeline system performance, physical pipeline condition, and cross-sector interdependencies. (Recommendation 6) |
In December 2018, we found that TSA used a risk ranking tool that calculated threat, vulnerability, and consequence for pipeline systems on variables such as the amount of throughput in the pipeline system. However, we also found that incorporating additional factors that enhance security into TSA's risk calculation would better align their efforts with federal policy. Therefore, we recommended that TSA identify or develop other data sources relevant to threat, vulnerability, and consequence and incorporate that data into its efforts to assess relative risk of critical pipeline systems, which could include data on prior attacks, natural hazards, feedback data on pipeline system performance, physical pipeline condition, and cross-sector interdependencies. In December 2023, TSA provided documentation and explanations for how the agency updated its risk ranking tool to address this recommendation. TSA added new data sources to the tool, such as refined data on pipeline support to electric power generation plants and additional information related to pipelines supporting defense installations. TSA also identified a range of supplementary data sources, originating from federal and non-federal sources and, in collaboration with an external contractor, evaluated the data's usefulness. Some of these data are under consideration for incorporation into the risk ranking tool in future years. As a result of these efforts, TSA is better positioned to identify pipeline relative risk and to more accurately target federal resources toward reducing vulnerabilities of high-risk pipeline networks.
|
| Transportation Security Administration |
Priority Rec.
The TSA Administrator should direct the Security Policy and Industry Engagement's Surface Division to take steps to coordinate an independent, external peer review of its Pipeline Relative Risk Ranking Tool, after the Pipeline Security Branch completes enhancements to its risk assessment approach. (Recommendation 7) |
In December 2018, we found that TSA's pipeline risk ranking tool had not been peer-reviewed since its conception in 2007. In our past work, we reported that independent, external peer reviews are a best practice in risk management and that independent expert review panels can provide objective reviews of complex issues. Therefore, we recommended that TSA take steps to coordinate an independent, external peer review of its pipeline risk ranking tool, after the agency completed enhancements to its risk assessment approach. According to TSA, in February 2023 the agency initiated a contract with a vendor to review and update the tool. One of the contract requirements was a complete review of the methodology, a task completed in June 2023 after TSA had made initial efforts to consult with other federal agencies on additional data sources for the tool. In December 2023, TSA provided documentation reflecting a peer review that proposed a methodology for updating the pipeline risk ranking tool and that further assessed available data sources. As a result of these efforts, TSA has better assurance that it can rank relative risk among pipeline systems using a more comprehensive and accurate methodology and additional information sources.
|
| Transportation Security Administration | The TSA Administrator should direct the Security Policy and Industry Engagement's Surface Division to ensure that it has a suite of performance measures which exhibit key attributes of successful performance measures, including measurable targets, clarity, and baseline and trend data. (Recommendation 8) |
We found that TSA established performance measures to monitor pipeline security review recommendations, analyze their results, and assess effectiveness in reducing risks. However, these measures did not possess key attributes--such as clarity, and having measurable targets--that GAO has found are key to successful performance measures. Therefore, we recommended that TSA develop a suite of performance measures which exhibit key attributes of successful performance measures, including measurable targets, clarity, and baseline and trend data. In response, TSA provided us its updated performance measures and documentation in August 2020 which explained the methodologies for calculating each measure. These measures are consistent with our recommendation. For example, several of the performance measures include measurable targets, such as 80 percent of cybersecurity assessments indicating compliance with TSA's relevant cybersecurity guidelines. Similarly, TSA documented a measure that evaluated the percentage of security drill and exercise activities that meet elements of TSA's pipeline security standards. The target performance level is 62 percent. TSA improved the clarity of its measures by documenting methodologies used for each measure, such that the methodology can be reviewed and linked to the performance measure language . For example, one measure is the percentage of physical security and access control measures that meet the elements in the TSA Pipeline Security Guidelines as assessed through TSA's security reviews. The measure's methodology is explained as the percentage of "Yes" responses to physical security and access control questions for companies or pipeline facilities who completed a security review from October 1, 2019 to present. Regarding baseline and trend data, TSA now documents baseline and trend information for measures in place for sufficient periods of time. For newer measures, this information will develop over time. By implementing these performance measure revisions and documenting the methodologies for their use, TSA is better positioned to assess its effectiveness at reducing pipeline systems' security risks.
|
| Transportation Security Administration | The TSA Administrator should direct the Security Policy and Industry Engagement's Surface Division to take steps to enter information on CSR recommendations and monitor and record their status. (Recommendation 9) |
We found that TSA conducts pipeline Corporate Security Reviews (CSRs), during which TSA staff make security-related recommendations to operators, if appropriate. For example, a CSR recommendation might include a suggestion to conduct annual security-related drills and exercises. However, TSA had not tracked the status of its pipeline recommendations for over 5 years. As a result, we recommended that TSA take steps to enter information on CSR recommendations and monitor and record their status. In April 2020, TSA provided documentation and explanations of actions taken to update and monitor CSR recommendations. Specifically, TSA issued a Pipeline Security Assessment Guidance document and a CSR Workbook to describe the process of conducting CSRs and entering information on CSR recommendations, monitoring and recording their status. In addition, TSA's follow-up database for CSR recommendations indicates updated recordings of recommendation status. TSA's actions are consistent with our recommendation.
|
| Transportation Security Administration | The TSA Administrator should direct the Security Policy and Industry Engagement's Surface Division to improve the quality of its pipeline security program data by developing written documentation of its data entry and verification procedures, implementing standardized data entry formats, and correcting existing data entry errors. (Recommendation 10) |
We found that TSA used several databases to store information related to TSA pipeline security assessments. We identified several problems with the databases that indicate that the pipeline security program data were not sufficiently reliable and do not provide quality information that is current, complete, and accurate. For example, one of the recommendation databases only included information for reviews conducted from November 2010 through February 2013 and data were missing or erroneously entered in many data entry fields. As a result, we recommended that TSA improve the quality of its pipeline security program data by developing written documentation of its data entry and verification procedures, implementing standardized data entry formats, and correcting existing data entry errors. In April 2020, TSA officials reported that they completed development of the Pipeline Security Assessment Guidance document and issued the Corporate Security Review (CSR) Workbook to describe the process of conducting CSRs and entering information on CSR recommendations, monitoring and recording their status. We reviewed and verified that these documents provide written documentation likely to improve the quality of information TSA uses in managing its pipeline security program. TSA's actions are consistent with our recommendation.
|
