Taxpayer Information: IRS Needs to Improve Oversight of Third-Party Cybersecurity Practices
Fast Facts
Each year, about 90% of people file their taxes using commercial software or a paid tax return preparer. If these "third parties" that handle your tax information are hacked, your personal information could be exposed—leaving you vulnerable to identity theft.
Some of these third parties may not know how to keep your information safe. Also, IRS doesn't have the same information security requirements for all software companies or for all paid preparers, so taxpayer information isn't consistently protected from hackers.
We recommended that IRS make its information security standards for third parties more consistent.

IRS tweet: Some scam emails link bogus IRS websites that look real. Be alert and stay informed.
Highlights
What GAO Found
Federal law and guidance require that the Internal Revenue Service (IRS) protect the confidentiality, integrity, and availability of the sensitive financial and taxpayer information that resides on its systems. However, taxpayer information held by third-party providers—such as paid tax return preparers and tax preparation software providers—generally falls outside of these requirements, according to IRS officials.
In 2018, about 90 percent of individual taxpayers had their tax returns electronically filed by paid preparers or used tax preparation software to prepare and file their own returns.
How Individual Tax Returns Were Filed, Calendar Year 2018

IRS seeks to help safeguard electronic tax return filing for various types of third-party providers through requirements under its Authorized e-file Provider program. However, IRS’s efforts do not provide assurance that taxpayers’ information is being adequately protected.
- Paid Preparers. IRS has not developed minimum information security requirements for the systems used by paid preparers or Authorized e-file Providers. According to IRS’s Office of Chief Counsel, IRS does not have the explicit authority to regulate security for these systems. Instead, the Internal Revenue Code gives IRS broad authority to administer and supervise the internal revenue laws. The Department of the Treasury has previously requested additional authority to regulate the competency of all paid preparers; GAO has also suggested that Congress consider granting IRS this authority. Congress has not yet provided such authority. Neither the Department of the Treasury request nor the GAO suggestion included granting IRS authority to regulate the security of paid preparers’ systems. Having such authority would enable IRS to establish minimum requirements. Further, having explicit authority to establish security standards for Authorized e-file Providers’ systems may help IRS better ensure the protection of taxpayers’ information.
- Tax Software Providers. As part of a public-private partnership between IRS and the tax preparation industry, 15 tax software providers voluntarily adhere to a set of about 140 information security controls developed using guidance from the National Institute of Standards and Technology (NIST). However, these controls are not required, and these providers represent only about one-third of all tax software providers. Additionally, IRS established six security, privacy, and business standards for providers of software that allows individuals to prepare their own tax returns (as opposed to software that paid preparers use). However, IRS has not substantially updated these standards since 2010, and they are, at least in part, outdated. For example, IRS cites an outdated encryption standard that NIST recommends not using due to its many known weaknesses.
A key factor contributing to missed opportunities to address third-party cybersecurity is IRS’s lack of centralized leadership. Consequently, IRS is less able to ensure that third-party providers adequately protect taxpayers’ information, which may result in identity theft refund fraud.
Example of Successful Identity Theft Refund Fraud Attempt
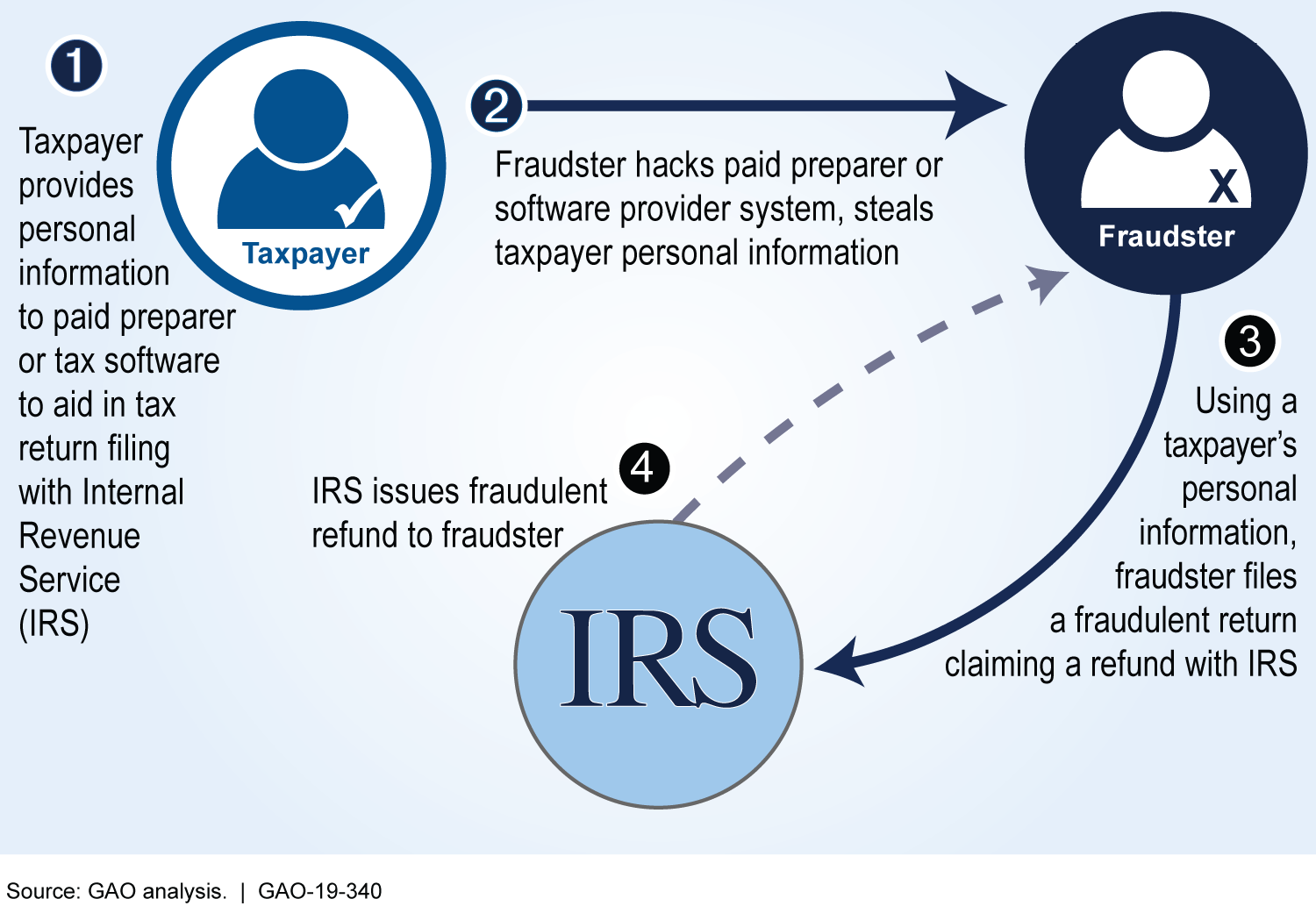
IRS monitors compliance with its electronic tax return filing program requirements for those paid preparers who electronically file returns; however, IRS’s monitoring has a limited focus on cybersecurity issues. For example, the monitoring techniques largely focus on physical security (e.g., locked filing cabinets) rather than verifying that preparers have an information security policy consistent with NIST-recommended controls. Without effective monitoring of cybersecurity controls, IRS has limited assurance that those paid preparers’ systems have adequate controls in place to protect clients’ data.
IRS recently began collecting information on high-risk security incidents, such as hackers infiltrating third-party provider systems. Reported incidents increased from 2017 to 2018, the only years for which IRS has data. However, IRS does not have a full picture of the scope of incidents because of inconsistent reporting requirements, including no reporting requirements for paid preparers.
Reported High-Risk Security Incidents at Paid Preparers and Tax Software Providers, 2017 and 2018
| 2017 | 2018 | |
| Number of security incidents | 212 | 336 |
| Number of taxpayer accounts affected | 180,557 | 211,162 |
GAO analysis of Internal Revenue Service data. | GAO-19-340
Why GAO Did This Study
Third-party providers, such as paid tax return preparers and tax preparation software providers, greatly impact IRS’s administration of the tax system. If these third parties do not properly secure taxpayers’ personal and financial information, taxpayers will be vulnerable to identity theft refund fraud and their sensitive personal information will be at risk of unauthorized disclosure. IRS estimates that it paid out at least $110 million in identity theft tax refund fraud during 2017, and at least $1.6 billion in identity theft tax refund fraud during 2016.
GAO was asked to review IRS’s efforts to track, monitor, and deter theft of taxpayer information from third parties. Among other things, this report assesses what is known about the taxpayer information security requirements for the systems used by third-party providers, IRS’s processes for monitoring compliance with these requirements, and IRS’s requirements for third-party security incident reporting.
GAO analyzed IRS’s information security requirements, standards, and guidance for third-party providers and compared them to relevant laws, regulations, and leading practices, such as NIST guidance and Standards for Internal Control in the Federal Government. GAO reviewed IRS’s monitoring procedures and its requirements and processes for third-party reporting of security incidents, and compared them to Internal Control Standards and GAO’s A Framework for Managing Fraud Risk in Federal Programs. GAO also interviewed IRS and tax industry group officials.
Recommendations
GAO suggests that Congress consider providing IRS with explicit authority to establish security requirements for paid preparers’ and Authorized e-file Providers’ systems.
GAO is also making eight recommendations, including that the Commissioner of Internal Revenue
- Develop a governance structure or other form of centralized leadership to coordinate all aspects of IRS’s efforts to protect taxpayer information while at third-party providers.
- Require all tax software providers to adhere to prescribed information security controls.
- Regularly review and update security standards for tax software providers.
- Update IRS’s monitoring programs to include basic cybersecurity issues.
- Standardize incident reporting requirements for all types of third-party providers.
IRS agreed with three recommendations, including the above recommendations to regularly review and update security standards for tax software providers, and standardize incident reporting requirements.
IRS disagreed with five recommendations—including the other three listed above—generally citing the lack of clear and explicit authority it would need to establish security requirements for the information systems of paid preparers and Authorized e-file Providers. GAO believes that IRS can implement these recommendations without additional statutory authority.
Matter for Congressional Consideration
| Matter | Status | Comments |
|---|---|---|
| Congress should consider providing IRS with explicit authority to establish security requirements for the information systems of paid preparers and Authorized e-file Providers. (Matter for Consideration 1) | In September 2021, a bill was introduced in the Senate (S.2782) that would require the Secretary of the Treasury to set cybersecurity standards for third party tax preparation companies to better protect taxpayer information, as well as requiring the Commissioner of the Internal Revenue Service to organize and coordinate all aspects of the Service's efforts to protect taxpayer information received from third-party preparers. However, as of January 2026 no further action has been taken on bills to provide IRS explicit authority to establish security requirements for the information systems of paid preparers and Authorized e-file Providers. |
Recommendations for Executive Action
| Agency Affected | Recommendation | Status |
|---|---|---|
| Internal Revenue Service |
Priority Rec.
The Commissioner of Internal Revenue should develop a governance structure or other form of centralized leadership, such as a steering committee, to coordinate all aspects of IRS's efforts to protect taxpayer information while at third-party providers. (Recommendation 1) |
IRS agreed with the intent of the recommendation but did not agree to implement it. In December 2025, IRS executives reiterated the need for additional explicit authority to establish security requirements for the information systems of paid preparers and others who electronically file returns. IRS reported that to effectively establish data safeguarding policies and implement strategies enforcing compliance with those policies, a centralized leadership structure requires the statutory authority that clearly communicates the authority of the IRS to do so. IRS stated that without such authority, implementing the recommendation would be an inefficient, ineffective, and costly use of resources. We continue to believe that IRS could implement this recommendation without additional statutory authority. IRS has ongoing activities aimed at protecting taxpayer information at third-party providers, and our recommendation is to coordinate such activities. We also disagree that convening a governance structure or other centralized form of leadership would be inefficient, ineffective, or costly. To fully implement this recommendation, IRS needs to develop a structure to coordinate across seven different offices working on information security-related activities, such as updating existing standards, monitoring Authorized e-file Provider program compliance, and tracking security incident reports. Without this structure, it is unclear how IRS can respond to changing security threats and ensure those threats are mitigated.
|
| Internal Revenue Service | The Commissioner of Internal Revenue should modify the Authorized e-file Provider program's requirements to explicitly state the required elements of an information security program as provided by the FTC Safeguards Rule. (Recommendation 2) |
In May 2019, we found that IRS had not fully incorporated the Federal Trade Commission (FTC) Safeguards Rule into its requirements for all provider types under the Authorized e-file Provider program. In August 2020, IRS updated its Publication 1345, Handbook for Authorized IRS e-file Providers of Individual Income Tax Returns to include more information on the FTC's Safeguard Rule including the Commission's authority, some basic security elements, and details where e-file providers can locate more information. The updates to this publication will help IRS ensure that all types of Authorized e-file Providers are aware of, and comply with, the FTC Safeguards Rule, which could help them better protect taxpayers' information.
|
| Internal Revenue Service | The Commissioner of Internal Revenue should require that all tax software providers that participate in the Authorized e-file Provider program follow the subset of NIST Special Publication 800-53 controls that were agreed upon by the Security Summit participants. (Recommendation 3) |
In its initial response to our draft report, IRS disagreed with this recommendation. In November 2019, IRS stated it was in agreement with the intent of this recommendation; however, IRS does not plan to implement it without additional statutory authority to require Authorized e-file Provider Program participants to comply with the NIST Special Publication 800-53. We continue to believe that under IRS's existing authority, IRS has already established some information security requirements for a portion of tax software providers, those that are online providers. IRS has the opportunity to further establish standards for all tax software providers by incorporating the subset of NIST controls into its Authorized e-file Provider program, which would capitalize on the work it has completed with the Security Summit members. As of December 2025, there are no additional status updates.
|
| Internal Revenue Service | The Commissioner of Internal Revenue should regularly review and update the security requirements that apply to tax software providers and other Authorized e-file Providers. (Recommendation 4) |
In May 2019, GAO found IRS did not have a robust set of information security requirements for all tax software providers in the Authorized e-file Provider program. Instead, IRS had limited security requirements for the subset of tax software providers designated as online providers. In August 2020, IRS updated its Publication 1345, Handbook for Authorized IRS e-file Providers of Individual Tax Returns. The update included six new security standards applicable to online providers in the Authorized e-file Providers Program. For example, online providers are required to run weekly external network vulnerability scans of all their systems. All providers in the program are required to report security incidences to IRS once detected. In addition, the Commissioner for Wage and Investment Division issued an internal memo requesting annual reviews of these standards as a part of the publication's annual review process. Periodically reviewing and updating the standards will help IRS ensure that the standards are keeping pace with technological changes, thereby helping online providers protect taxpayer data.
|
| Internal Revenue Service | The Commissioner of Internal Revenue should update IRS's monitoring programs for electronic return originators to include techniques to monitor basic information security and cybersecurity issues. Further, IRS should make the appropriate revisions to internal guidance, job aids, and staff training, as necessary. (Recommendation 5) |
In its initial response to our draft report, IRS disagreed with this recommendation. In November 2019, IRS stated it was in agreement with the intent of this recommendation; however, it does not plan to implement it. IRS reported it does not have the statutory authority to establish policy on information security and cybersecurity issues, nor to enforce compliance if noncompliance is observed. Additionally, IRS said that the specialized technical skills required to monitor compliance with information and cybersecurity standards, should statutory authority be granted, would require additional funding to meet those monitoring needs. However, as we reported, IRS already monitors physical aspects of information security, which goes beyond existing Authorized e-file Provider program requirements. Since most individuals now file tax returns electronically, having checks for physical security without comparable checks for cybersecurity does not address current risks, as cyber criminals and fraudsters are increasingly attacking third-party providers, as IRS has noted. We believe that incorporating some basic cybersecurity monitoring into the visits would provide IRS the opportunity to help inform the most vulnerable third-party providers of additional guidance and resources. As of December 2025, there are no additional status updates.
|
| Internal Revenue Service | The Commissioner of Internal Revenue should conduct a risk assessment to determine whether different monitoring approaches are appropriate for all of the provider types in the IRS's Authorized e-file Provider program. If changes are needed, IRS should make appropriate revisions to the monitoring program, internal guidance, job aids, and staff training, as necessary. (Recommendation 6) |
In its initial response to our draft report, IRS disagreed with this recommendation. In November 2019, IRS said it agreed with the intent of this recommendation; however it does not plan to implement it. IRS stated that absent statutory authority and funding, an assessment of the different monitoring approaches is moot. We disagree with this conclusion. As discussed in the report, IRS does not systematically monitor the existing security requirements for online providers, nor does it conduct information security or cybersecurity monitoring for all types of Authorized e-file Providers. We believe that IRS could conduct a risk assessment of its current monitoring program within existing statutory authority and make necessary changes that would provide better assurance that all types of providers are receiving some level of oversight and that IRS is addressing the greatest risk areas appropriately. As of December 2025, there are no additional status updates.
|
| Internal Revenue Service | The Commissioner of Internal Revenue should standardize the incident reporting requirements for all types Authorized e-file Providers. (Recommendation 7) |
In May 2019, GAO found that IRS did not have comprehensive information about the security incidents because, in part, its reporting requirements do not apply to all third-party providers. In August 2020, IRS updated Publication 1345: Handbook for Authorized IRS e-file Providers of Individual Tax Returns to include a standardized reporting requirement for all types of Authorized e-file providers. Among the requirements are to include specifics on the timing of the incident, number of taxpayers affected, and whether taxpayer information was disclosed. The addition of a clear and standardized reporting requirement for all types of providers will help IRS have more assurance that third-party providers consistently report their security incidents in a timely manner. This in turn will help IRS better understand the size and scope of information security incidents, which it uses to protect compromised individual taxpayer accounts and prevent identity theft refund fraud.
|
| Internal Revenue Service | The Commissioner of Internal Revenue should document intake, storage, and sharing of the security incident data across IRS offices. (Recommendation 8) |
In May 2019, we reported that the Internal Revenue Service (IRS) did not document processes for third party provider security incident reporting or data storage. For example, security incident information submitted to multiple offices eventually moved to an Incident Management Database, though multiple databases may have contained information about the same incident. Before adding a new incident to the Incident Management Database, staff conducted a query in the database to ensure that the incident was not already added. However, IRS had not documented how the security incident data processes should flow, relying instead on informal communication efforts of the staff and the assumption that staff knew where the data belonged and would provide that information to the appropriate offices. We recommended that the Commissioner of Internal Revenue should document intake, storage, and sharing of the security incident data across IRS offices. In response, IRS took steps to address this recommendation in November 2019 by, for example, publishing guidance about the formal process for tax professionals to report security incidents to IRS Stakeholder Liaisons. IRS documented its procedures in the Data Breach Incident Report Instructions that Stakeholder Liaison staff follow during the intake process. Upon completion, the security incident information is disseminated to other offices within the IRS, depending on the nature of the breach incident reported. Guidance provided to Stakeholder Liaison staff notes that security incident information will be shared with several offices including Return Integrity and Compliance Services, Criminal Investigation, E-Services, and the Return Preparer Office. In 2021, IRS officials also informed us about its automatic forwarding rule to ensure incidents that are submitted to IRS are sent to the correct department. Steps such as these help IRS ensure that security incidents are properly recorded and monitored in IRS systems, and may allow for more complete data as the data would follow a specific routing and review process.
|
