Information Security: Better Implementation of Controls for Mobile Devices Should Be Encouraged
Highlights
What GAO Found
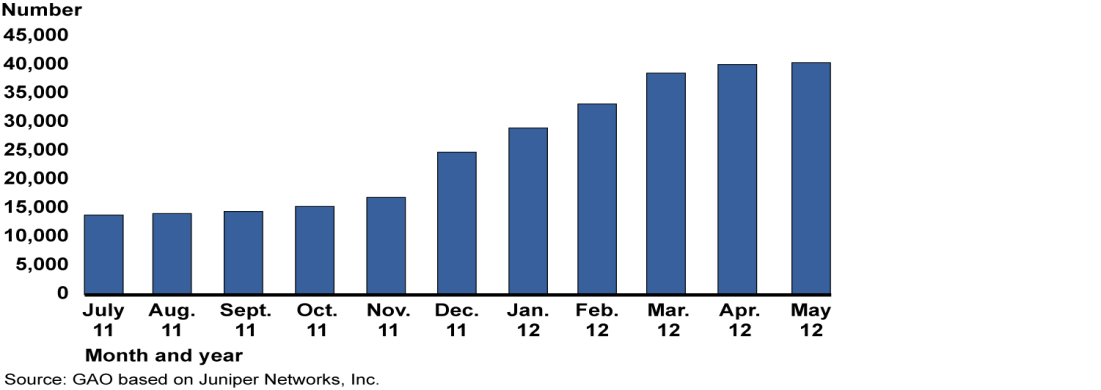
Threats to the security of mobile devices and the information they store and process have been increasing significantly. For example, the number of variants of malicious software, known as “malware,” aimed at mobile devices has reportedly risen from about 14,000 to 40,000 or about 185 percent in less than a year (see figure). Cyber criminals may use a variety of attack methods, including intercepting data as they are transmitted to and from mobile devices and inserting malicious code into software applications to gain access to users’ sensitive information. These threats and attacks are facilitated by vulnerabilities in the design and configuration of mobile devices, as well as the ways consumers use them. Common vulnerabilities include a failure to enable password protection and operating systems that are not kept up to date with the latest security patches.
Figure: Number of Malware Variants Identified Globally between July 2011 and May 2012
Mobile device manufacturers and wireless carriers can implement technical features, such as enabling passwords and encryption to limit or prevent attacks. In addition, consumers can adopt key practices, such as setting passwords and limiting the use of public wireless connections for sensitive transactions, which can significantly mitigate the risk that their devices will be compromised.
Federal agencies and private companies have promoted secure technologies and practices through standards and public private partnerships. Despite these efforts, safeguards have not been consistently implemented. Although the Federal Communications Commission (FCC) has facilitated public-private coordination to address specific challenges such as cellphone theft, it has not yet taken similar steps to encourage device manufacturers and wireless carriers to implement a more complete industry baseline of mobile security safeguards. In addition, many consumers still do not know how to protect themselves from mobile security vulnerabilities, raising questions about the effectiveness of public awareness efforts. The Department of Homeland Security (DHS) and National Institute of Standards and Technology (NIST) have not yet developed performance measures or a baseline understanding of the current state of national cybersecurity awareness that would help them determine whether public awareness efforts are achieving stated goals and objectives.
Why GAO Did This Study
Millions of Americans currently use mobile devices—e.g., cellphones, smartphones, and tablet computers—on a daily basis to communicate, obtain Internet-based information, and share their own information, photographs, and videos. Given the extent of consumer reliance on mobile interactions, it is increasingly important that these devices be secured from expanding threats to the confidentiality, integrity, and availability of the information they maintain and share.
Accordingly, GAO was asked to determine (1) what common security threats and vulnerabilities affect mobile devices, (2) what security features and practices have been identified to mitigate the risks associated with these vulnerabilities, and (3) the extent to which government and private entities have been addressing the security vulnerabilities of mobile devices. To do so, GAO analyzed publically available mobile security reports, surveys related to consumer cybersecurity practices, as well as statutes, regulations, and agency policies; GAO also interviewed representatives from federal agencies and private companies with responsibilities in telecommunications and cybersecurity.
Recommendations
GAO recommends that FCC encourage the private sector to implement a broad, industry-defined baseline of mobile security safeguards. GAO also recommends that DHS and NIST take steps to better measure progress in raising national cybersecurity awareness. The FCC, DHS, and NIST generally concurred with GAOs recommendations.
Recommendations for Executive Action
| Agency Affected | Recommendation | Status |
|---|---|---|
| Federal Communications Commission | To help mitigate vulnerabilities in mobile devices, the Chairman of the Federal Communications Commission should continue to work with wireless carriers and device manufacturers on implementing cybersecurity best practices by encouraging them to implement a complete industry baseline of mobile security safeguards based on commonly accepted security features and practices. |
In response to our recommendation, the FCC tasked the Communications Security, Reliability, and Interoperability Council (CSRIC) to update the cybersecurity best practices. The council developed voluntary mechanisms that increase assurance that communication providers are taking the necessary measures to manage cybersecurity risks across the enterprise, and to provide implementation guidance to help communication providers use and adapt the voluntary NIST Cybersecurity Framework. As a result, the FCC has increased assurance that companies can mitigate known security vulnerabilities in mobile devices.
|
| Federal Communications Commission | To help mitigate vulnerabilities in mobile devices, the Chairman of the Federal Communications Commission should monitor progress of wireless carriers and device manufacturers in achieving their milestones and time frames once an industry baseline of mobile security safeguards has been implemented. |
As of May 2019, FCC has not implemented the recommendation. Moreover, the agency has not demonstrated an intent to address the recommendation.
|
| Department of Homeland Security | To determine whether the NICE initiative is having a beneficial effect in enhancing consumer awareness of mobile security issues, the Secretary of Homeland Security in collaboration with the Secretary of Commerce should establish a baseline measure of consumer awareness and behavior related to mobile security. |
In September 2013, DHS as part of its NICE initiative through the Stop-Think-Connect Campaign, developed an online survey of millennials' behavior, which included several questions about mobile device use. The final report was used to gain insights about baseline awareness and behaviors, and the raw analysis also measured respondents' awareness of the Stop-Think-Connect Campaign. The campaign intends to continue issuing the survey each year during National Cyber Security Awareness Month to measure changes from the baseline. Thus the survey provides DHS a baseline measure of consumer awareness and behavior related to mobile security.
|
| Department of Homeland Security | To determine whether the NICE initiative is having a beneficial effect in enhancing consumer awareness of mobile security issues, the Secretary of Homeland Security in collaboration with the Secretary of Commerce should develop performance measures that use the awareness baseline to assess the effectiveness of the awareness component of the NICE initiative. |
In response to our recommendation, DHS, as part of its NICE initiative, established in 2013 several metrics to determine its reach and effectiveness, including the number of individuals that opt-in to receive campaign materials, the number of non-profit organizations, governments, and academic institutions that officially partner with the campaign, the number of website hits to the campaign and National Cyber Security Awareness Month web pages, and the number of events held for the campaign and National Cyber Security Awareness Month. According to DHS officials, these metrics are measured on an ongoing basis throughout the year to assess the effectiveness of the awareness component of the NICE initiative.
|
