Nuclear Weapons Cybersecurity: NNSA Should Fully Implement Foundational Cybersecurity Risk Management Practices
Fast Facts
The National Nuclear Security Administration (NNSA) is increasingly relying on advanced computers and integrating digital systems into weapons and manufacturing equipment. But, these systems could be hacked.
Federal laws and policies suggest 6 key practices to set up a cybersecurity management program, such as assigning risk management responsibilities. However, NNSA and its contractors haven't fully implemented these practices.
Additionally, NNSA and its contractors rely on subcontractors for services and equipment, but we found that oversight of subcontractors' cybersecurity was inconsistent. Our recommendations address these issues.
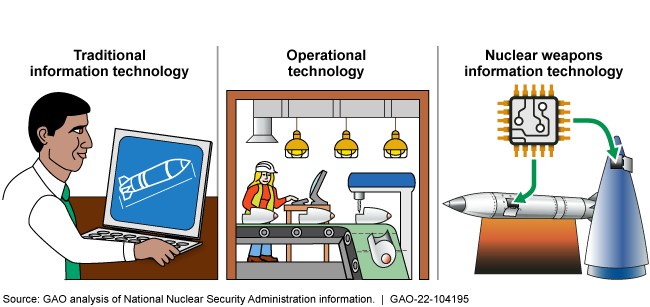
National Nuclear Security Administration Digital Environments
Highlights
What GAO Found
The National Nuclear Security Administration (NNSA) and its contractors have not fully implemented six foundational cybersecurity risk practices in its traditional IT environment. NNSA also has not fully implemented these practices in its operational technology and nuclear weapons IT environments.
Organization-wide Foundational Practices to Manage Cybersecurity Risk
|
Practice 1 |
Identify and assign cybersecurity roles and responsibilities for risk management. |
|
Practice 2 |
Establish and maintain a cybersecurity risk management strategy for the organization. |
|
Practice 3 |
Document and maintain policies and plans for the cybersecurity program. |
|
Practice 4 |
Assess and update organization-wide cybersecurity risks. |
|
Practice 5 |
Designate controls that are available for information systems or programs to inherit. |
|
Practice 6 |
Develop and maintain a strategy to monitor risks continuously across the organization. |
Source: GAO analysis based on Office of Management and Budget, National Institute of Standards and Technology, and Committee on National Security Systems guidance. | GAO-22-104195
The traditional IT environment includes computer systems used for weapons design. NNSA fully implemented four of six practices and partially implemented two. NNSA contractors had fully implemented three of six practices and did not fully implement three. For example, both NNSA and its contractors had not fully implemented a continuous monitoring strategy because their strategy documents were missing key recommended elements. Without such elements, NNSA and its contractors lack a full understanding of their cybersecurity posture and are limited in their ability to effectively respond to emerging cyber threats.
The operational technology environment includes manufacturing equipment and building control systems with embedded software to monitor physical devices or processes. NNSA has not yet fully implemented any foundational risk management practices in this environment, and it is still developing specific guidance for contractors. This is partially because NNSA has not yet determined the resources it needs to implement practices and develop guidance.
The nuclear weapons IT environment includes IT in or in contact with weapons. NNSA has implemented or taken action consistent with implementing most of the practices in this environment and is developing specific guidance for contractors. However, NNSA has not developed a cyber risk management strategy to address nuclear weapons IT-specific threats. The absence of such a strategy likely constrains NNSA's awareness of and responses to such threats.
NNSA's cybersecurity directive requires contractors to oversee their subcontractors' cybersecurity measures, but contractors' efforts to provide such oversight are mixed, and three of seven contractors do not believe it is a contractual responsibility. An NNSA official proposed adding an evaluation of such oversight to its annual contractor performance evaluation process, but NNSA could not provide evidence that it had done so. These oversight gaps, at both the contractor and NNSA level, leave NNSA with little assurance that sensitive information held by subcontractors is effectively protected.
Why GAO Did This Study
NNSA and its site contractors integrate information systems into nuclear weapons, automate manufacturing equipment, and rely on computer modeling to design weapons. However, cyber systems are targets of malicious actors. To protect against such threats, federal law and policies require that NNSA establish a program to manage cybersecurity risk, which includes the implementation of six foundational practices. NNSA contractors are required to oversee subcontractors' cybersecurity.
The Senate committee report accompanying the National Defense Authorization Act for Fiscal Year 2020 included a provision for GAO to review NNSA's cybersecurity practices and policies, and GAO was also asked to perform similar work. GAO's report examines the extent to which (1) NNSA and its seven site contractors implemented foundational cybersecurity risk management practices and (2) contractors oversee subcontractor cybersecurity.
GAO reviewed NNSA and contractor documents, compared NNSA's efforts with federal and agency requirements for risk management practices, and interviewed NNSA officials and contractor representatives.
Recommendations
GAO is making nine recommendations to NNSA, including that it fully implement an IT continuous monitoring strategy; determine needed resources for operational technology efforts; create a nuclear weapons risk strategy; and enhance monitoring of subcontractor cybersecurity. NNSA agreed with GAO's recommendations.
Recommendations for Executive Action
| Agency Affected | Recommendation | Status |
|---|---|---|
| National Nuclear Security Administration | The NNSA Administrator should promptly finalize its planned revision of Supplemental Directive 205.1, Baseline Cybersecurity Program, to include the most relevant federal cybersecurity requirements and review the directive at least every 3 years. (Recommendation 1) |
In September 2024, NNSA issued its updated Baseline Cybersecurity Program, Supplemental Directive 205.1A, which includes relevant requirements of a cybersecurity program, and extends such requirements to the range of NNSA's IT systems, including nuclear weapons IT, IT associated with operational technology, and other NNSA national security systems.
|
| National Nuclear Security Administration | The NNSA Administrator should direct NNSA's Office of Information Management, and the site contractors that have not done so, to develop and maintain cybersecurity continuous monitoring strategies that address all elements from NIST guidance. (Recommendation 2) |
NNSA agreed with and has taken steps to implement our recommendation. In May 2024, NNSA revised its Enterprise Cybersecurity Program Plan. In addition, in September 2024 NNSA issued a revised version of Supplemental Directive 205.1 and its Multi-Year Cybersecurity Program Execution Guidance. Collectively, these documents demonstrate that NNSA-IM has directed the NNSA-wide cybersecurity program and site contractors to develop and maintain continuous monitoring strategies that address recommended elements from NIST SP 800-37. By taking these steps, NNSA has greater assurance that a comprehensive cyber risk management framework exists for the nuclear security enterprise.
|
| National Nuclear Security Administration | The NNSA Administrator should direct NNSA's Office of Information Management, and the site contractors that have not done so, to identify and assign all risk management roles and responsibilities called for in NIST guidance. (Recommendation 3) |
NNSA agreed with and has taken steps to implement our recommendation. In May 2024, NNSA revised its Enterprise Cybersecurity Program Plan. In addition, in September 2024 NNSA issued a revised version of Supplemental Directive 205.1 and its Multi-Year Cybersecurity Program Execution Guidance. Collectively, these documents demonstrate that NNSA-IM has directed the NNSA-wide cybersecurity program and site contractors to identify and assign all risk management roles and responsibilities called for in NIST SP 800-37 guidance. By taking these steps, NNSA has greater assurance that a comprehensive cyber risk management framework exists for the nuclear security enterprise.
|
| National Nuclear Security Administration | The NNSA Administrator should direct that the site contractors that have not done so maintain a site-wide cybersecurity risk management strategy that addresses all elements from NIST guidance and perform periodic reviews at least annually. (Recommendation 4) |
NNSA agreed with and has taken steps to implement our recommendation. In May 2024, NNSA revised its Enterprise Cybersecurity Program Plan. In addition, in September 2024 NNSA issued a revised version of Supplemental Directive 205.1 and its Multi-Year Cybersecurity Program Execution Guidance. Collectively, these documents demonstrate that NNSA-IM has directed the NNSA-wide cybersecurity program and site contractors to maintain a site-wide cybersecurity risk management strategy that addresses all elements from NIST SP 800-37 guidance and perform periodic reviews at least annually. By taking these steps, NNSA has greater assurance that a comprehensive cyber risk management framework exists for the nuclear security enterprise.
|
| National Nuclear Security Administration |
Priority Rec.
The NNSA Administrator should direct the Office of Information Management to identify the needed resources to implement foundational practices for the OT environment, such as by developing an OT activity business case for consideration in NNSA's planning, programming, budgeting, and evaluation process. (Recommendation 5) |
NNSA agreed with our recommendation and, in November 2022, stated that needed resources would be identified for developing an Operational Technology (OT) business case for use in the budgeting process. In July 2024, NNSA officials provided us with information that showed the agency had developed a business case in February 2024 to identify the required resources to implement cybersecurity foundational practices for the OT environment, consistent with our recommendation. In conjunction with the business case, NNSA officials also reported that an OT monitoring capability which had been previously piloted to assess OT security risks and identify required resources had been integrated into NNSA's planning, programming, budgeting, and execution (PPBE) process.
|
| National Nuclear Security Administration | The Director of NNSA's Office of Defense Programs should establish a cybersecurity risk management strategy for nuclear weapons information technology that includes all elements from NIST guidance. (Recommendation 6) |
NNSA agreed with our recommendation and, in November 2022, stated that it would develop a cybersecurity risk management strategy for nuclear weapons information technology. In June 2023, NNSA estimated it would complete this work by September 30, 2023. In January 2024, NNSA notified us that it had taken actions consistent with this recommendation, and provided us with a copy of a September 2023 strategy document entitled, "National Nuclear Security Administration (NNSA) Nuclear Weapon Information Technology (NWIT) Cyber Assurance Strategy." The document lays out NNSA's strategy for managing cyber-related risks to nuclear weapons, incorporates elements of NIST guidance, and notes that the strategy was prepared specifically in response to our recommendation.
|
| National Nuclear Security Administration |
Priority Rec.
The Director of NNSA's Office of Acquisition and Project Management should clarify and reinforce to the M&O contractors, such as by a policy flash or other communication, that they are required to monitor subcontractor's cybersecurity measures. (Recommendation 7) |
NNSA agreed with our recommendation. In December 2022, NNSA clarified M&O contractors' responsibility to validate subcontractor compliance with cybersecurity requirements in its fiscal year 2023 Cybersecurity Program Execution Guidance. In September 2024, NNSA issued its revised Supplemental Directive 205.1, Baseline Cybersecurity Policy, which contained additional guidance for contractors specifying that they should implement a program to ensure the ongoing monitoring of cybersecurity requirements for all subcontractors. In addition, the directive specified that subcontractor cybersecurity oversight measures must be included in the annual contractor performance evaluation process.
|
| National Nuclear Security Administration |
Priority Rec.
The Director of NNSA's Office of Acquisition and Project Management should include performance criteria evaluating contractor oversight of subcontractor cybersecurity measures in the annual M&O contractor performance evaluation process. (Recommendation 8) |
NNSA agreed with our recommendation. In December 2022, NNSA issued its fiscal year 2023 Cybersecurity Program Execution Guidance--which provides performance details for the high-level performance statement contained within NNSA's performance evaluation process. This revised guidance explicitly clarified M&O contractors' responsibility to validate subcontractor compliance with cybersecurity requirements.
|
| National Nuclear Security Administration | The NNSA Administrator should direct Information Management and the Office of Acquisition and Project Management to ensure that Supplemental Directive 205.1 contains language requiring third-party validation of contractor and subcontractor cybersecurity measures. (Recommendation 9) |
NNSA agreed with and has taken steps to implement our recommendation. In addition, in September 2024 NNSA issued a revised version of Supplemental Directive 205.1. The supplemental directive requires contractors to flow down baseline cybersecurity requirements to subcontractors. In addition, the supplemental directive requires contractors to implement a risk managed approach to subcontractor requirements and monitoring program that is defined, documented, and approved by the appropriately designated Authorizing Official and the NNSA Chief Information Security Officer, ensuring that implementation and ongoing monitoring of cybersecurity requirements related to IT, OT, and service contracts are implemented for all subcontractors. By taking these steps, NNSA has greater assurance that a comprehensive cyber risk management framework exists for the nuclear security enterprise.
|
